A few weeks ago, a friend of of mine told me she needed a SSL certificate for her WooCommerce/Wordpress site. This is pretty much how the conversation went:
Me: Why do you need a SSL certificate?
Her: So I can have the checkout on my site.
Me: Why do you want to have checkout on your site?
Her: Because it looks better, to have it all on the one site and branded like my site.
Me: Where did you hear this?
Her: Well the industry group I’m in, they were all talking about. They are all going that way, of having the checkout on their site.
Me: These are people working on their own sites, and now they are adding SSL and in-house checkout themselves?
Her: Yeah, I guess.
Me: What’s wrong with the Paypal checkout?
Her: Well it looks less professional, and some people don’t like it.
At this point in the conversation, as a developer, you have to understand that I’m a little scared for these people. They all decided that one solution looked better and now they’re going to implement it without any sort of technical help or direction. And as my readers already know, I’m a huge fan of not storing any financial data. To add to that, I’m going to tell you why I’m also not a fan of people hosting checkout on their own site.
Just recently, WooThemes announced that they had a breach in their security system which allowed many credit card numbers to be intercepted by a 3rd party and then used fraudulently around the globe. (If you were involved in this, they should have already notified you.) But WooThemes is not alone in this, as these kind of breaches seem to happen on a daily basis — even with much bigger companies involved.
To put it in simple terms: The problem is called a man-in-the-middle attack, where a script somehow makes it onto your server and intercepts the card information between the point where you click submit on the web site and the card info arrives at the payment processor. So even though SSL is in use, and an offsite payment processor is being used, there is still a possibility of interception between the two sites.
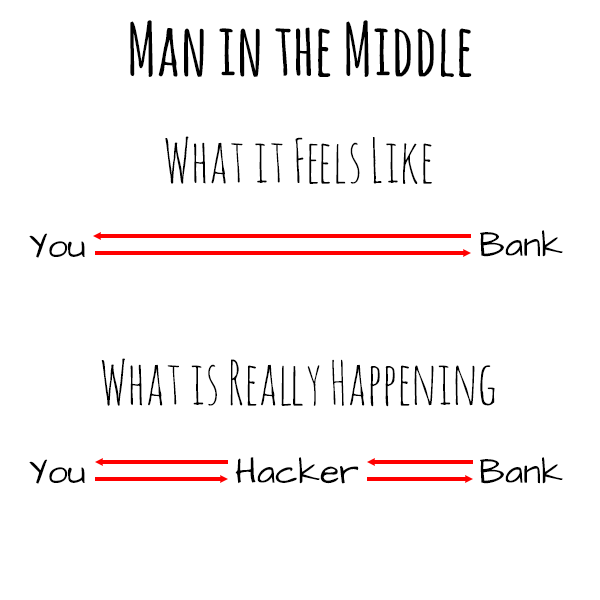
Let’s use this example and get back to my friend’s group. These big companies and these development companies have all the resources in the world: talented programmers, security experts, very expensive hosting solutions, and so on. And they still get hacked. What do you think your odds are of staying safe when you are self-installing a 3rd party payment and SSL solution on your shared hosting account? I’ll let you do the math on that one yourself.
The bottom line is this: Don’t do it.
Have I set up onsite payment systems for people in the past? Sure.
Would I openly recommend it to anyone? No.
Is it a bad idea for a majority of my clients? You bet.
I spend a lot of time in my work cleaning up the mess of other developers and hosting companies, and the site owner is often blindsided by the problems that exist. The truth is that many people who make websites out there for others do not know what they are doing, and they are setting up situations with great potential for leaking financial information. These situations hurt the customers and the business.
For the above reasons, I completely am against people having checkouts with SSL on their own sites — even if some guru or their networking group or some developer or whoever told them to do it.
So what should you be doing instead?
- Use an offsite payment processor. If you aren’t 100% sure about your security, just take the easiest route and have your payments processed offsite somewhere like PayPal, PaySimple, Infusionsoft, or Wufoo. This way, the financial data never even touches your shared hosting.
- Use reliable hosting. If you’re not sure about your hosting company, please just ask!
- Get a security audit to make sure you don’t have any interception scripts already installed on your site. Even without checkout on your site, interception scripts can steal information like your contact form submissions and use those e-mails for spam.
Questions?
As always, feel free to ask in the comments below!
